TCP/IP - Internet Transport Services
Intro and Background
Originally developed as a research experiment, TCP/IP has matured to become the backbone of the Information superhighway.
The TCP/IP protocols provide user's with the backbone services used to carry popular services such as the World Wide Web (WWW), E-Mail, and
others. From its beginnings in the late 70's as a U.S. Government Advanced Research Projects Agency (ARPA) research and development project, the "ARPANET" has grown to
provide connections to systems world wide, helping bring the information age into reality.
With a layered architecture, the TCP/IP suite can be understood as a set of discrete components. The lower layers (transport and below) of the TCP/IP suite can be viewed as shown in
Figure 1. The following sections cover the link, internetwork, and transport protocols. The link protocols provide the delivery of packets between adjacent nodes in an
internetwork; this delivery only implies that delivered information is intact, not that it has arrived in any particular order or that delivery guarantees are implied. The internetwork layer is
responsible for the addressing and routing of packets between source and destination nodes within the network. Finally, the transport layer provides a range of services to transfer
information between. As shown in Figure 1, the Internet applications make use of a combination of the services provided by TCP and/or UDP.
Other transport protocols have surfaced.
However, none have taken as prominent a role as TCP and UDP.
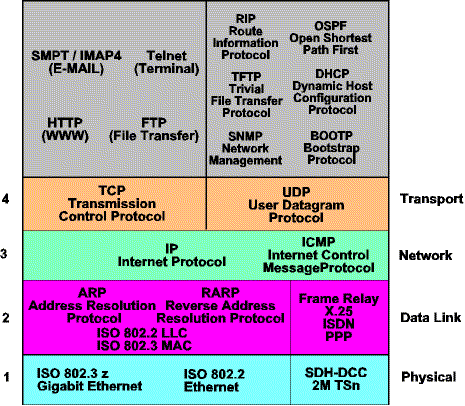
Figure 1 - Internet Protocol Suite - Architecture
Transport Services
Two general classes of transport services are most often associated with the Internet protocol suite, the Transmission Control Protocol (TCP), and the User Datagram Protocol (UDP).
Both of these protocols provide multiplexing services that permit the transmission of information to any one of a number of applications residing on the addressed hosts. UDP provides
an inherently unreliable packet transfer service, and TCP is a more full-featured protocol, providing reliable delivery of a information stream.
UDP, as its name suggests, is a datagram protocol that will make a single attempt to transfer every application packet to the appropriate destination, if the network is operating
efficiently, most packets will reach their destination. UDP is used by application protocols such as the Simple Network Management Protocol that supports network management, the
Trivial File Transfer Protocol. The UDP Header, is quite simple, specifying only the length of the datagram and identifying the source and destination ports that are involved in the
conversation.
TCP has been developed to support applications requiring reliable, ordered delivery of information between two participating network entities. Unlike UDP's packet orientation, TCP is a
byte oriented stream protocol, with all information acknowledgments being based on acknowledgment of individual bytes in the stream rather than complete packets. The protocol has
been designed to automatically adjust to differences in the communication channels that exist between the two processes participating in a conversation over the network. A sliding
window acknowledgment scheme controls the orderly delivery of information presented to the TCP stream. Retry timers are based entirely on route turnaround times, with exponential
increases being applied to the time applied to each subsequent retransmission of information.
Network Services
The Internet Protocol network layer provides the smarts required to identify the computers and subnetworks that receive and transmit packets. Services provided within the network
layer include packet addressing, routing of traffic between systems. Protocols that are important in providing these services include the Internet Protocol (the IP of TCP/IP), a series of
routing support protocols that help in identifying the most appropriate route for each packet in the network, and additional control protocols.
The current addressing scheme provided by IP makes use of a 32-bit address field that can be divided into up to four eight bit fields that are used to describe the network a host is
participating in, with a local address that specifies the address of the specific unit. Three types of direct station address formats are supported by IP, class A, in which the high-order 8
(actually seven) bits are used to describe the network, class B, in which the high-order 16 bits defining the network, and the low order 16 defining the host, and class C addresses, in
which the high-order 21 bits define the subnetwork, and the low order 8 bits define the specific hosts (machines) on the local network. The type of address is defined by the high-order
bits in the address. A zero in the highest order bit indicates Class A addressing, a 0x10 in the high-order two bits indicates that the address is a class B address. Class C addresses are
defined as having a 0x110 in the high-order three bits of the address. The next generation Internet protocols, still under active discussion, have addressed the limitations of these
addressing schemes through the definition of address spaces that can be scaled as the network size grows.
In addition to addressing and delivery of packets, IP provides fragmentation and reassembly services. Each link in the network has a parameter termed the Maximum Transmission Unit
(MTU) that represents the largest payload that can be carried. When upper layer packets exceed these values, the IP includes services that split each packet into two or more packets
that are subsequently routed through the network. Reassembly of the packets can occur either within a local network, or more typically can be reassembled at the receiving host. Timing
information is transferred with each IP packet to permit intermediate and end nodes on a route to identify and discard stale packets.
With IP providing only a small set of addressing, fragmentation, and reassembly services, additional route and link management services are required. For error reporting and fault
diagnosis, the Internet Control Message Protocol (ICMP) is frequently used.
Packet routing through the Internet is handled through a variety of techniques. In the simplest case, a system with no routing services directs all traffic through a single gateway that in
turn is responsible for determining the most appropriate routes. A key distinction in the definition of routing services is between autonomous networks attaching to the network
through a single access point, and internal network routing that can involve several routing choices. These routing protocols are grouped into the External Gateway Protocols (EGP) for
attaching autonomous networks to the Internet, and Internal Gateway Protocols that manage more complicated routing decisions within a network.
The EGP is used to exchange routing information between autonomous systems. The routing lists consist of a list of subnetworks that can be reached through the reporting gateway.
These reports are limited to only those subnetworks and hosts that the gateway provides direct service to (its own autonomous network) and not those destinations made available by
the peer gateways.
For more sophisticated routing services, the Internal Gateway Protocols actively compute reachability and cost information to gain access to other systems on the network. Two general
algorithms are used to perform this service, a distance vector algorithm, and a shortest path first (SPF) algorithm. In a distance vector based system, each routing node recalculates and
reports cost information to reach the destination nodes, paring its tree to some predetermined number of hops. The Route Information Protocol (RIP) is based on the simpler distance
vector algorithm. In an effort to provide additional standardization and a more robust set of services, the Open SPF (OSPF) protocol has been proposed in a separate set of Requests For
Comment (RFC).
Link Services
At the link-level, the Internet protocols need only provide delivery of completed packets. While reliable service can be implemented, it is not necessary, and in some cases could
actually impede the performance of TCP/IP based systems with additional retransmissions. Where reliability is required, TCP based services are generally used. Standards for exchange
of Internet traffic have been developed for a large number of physical links including ethernet, serial lines, Token Ring LANs, ATM, ISDN and others.
The Point To Point protocol is often used to support the exchange of IP packets between interconnected nodes. In general the link protocol services include mechanisms to
perform the following:
- Intact delivery - all information that is delivered is as intended by the sending station.
- Address binding - services are usually provided to map physical connections (such as ethernet addresses, phone numbers, stations...) with the Internet address. One of the
better known mechanisms for address binding is the Address Resolution Protocol (ARP), that maps IP addresses to ethernet addresses.
- Security - some of the link protocols include access authorization mechanisms. This is particularly important in the case of dial-in protocols, where some form of protection is
often required to protect critical network resources against unauthorized use.
For effective communication, the link services should provide a reasonable level of reliability. While the upper layer protocols have been designed to operate under a range of error
environments, frequent errors can result in annoying, and sometimes unpredictable system performance.
Boot Services
Several boot service protocols have been developed to help new nodes learn their role in a network, and to inform the network of their presence. In many cases, such as dial-up
protocols, diskless workstations, and embedded systems, a node entering a TCP/IP network may not have a preassigned network address. Some of the more popular boot protocols
include:
- Reverse Address Resolution Protocol (RARP) - one of the earlier booting protocols, RARP allows a station that knows its own physical ethernet address to request an IP
address from a RARP server. This protocol is still in use, with its popularity on a decline due to the fact that its services are limited to ethernet equipped devices, and no
standard mechanism for defining a boot file image.
- BOOTP - addresses the limitations of RARP, providing address discovery to systems not containing an Ethernet port, and provides a mechanism for the BOOTP server to
provide the diskless equipment with a name for the bootstrap code image. It is up to the client equipment to know how to process the received boot image name. Most typically,
the image is downloaded through a file transfer protocol such as the Trivial File Transfer Protocol (TFTP). Also, unlike RARP, BOOTP relies on UDP and IP for the transfer of its
requests. This permits operation in installations that may include several local subnets with a single centralized BOOTP server.
- the Dynamic Host Configuration Protocol (DHCP) further extends the services provided by BOOTP to permit the negotiation and transfer of operating parameters to the booting
client system.
Application Transport Selections
The Internet applications typically use either UDP or TCP, with the rationale for the use of the different protocols depending on the nature of the application. Where reliable information
with a specific connection context is required, TCP is the preferred protocol. Examples of application protocols that use UDP are Telnet, Rlogin, and the File Transfer Protocol. These
application protocols have been designed to leverage the reliable connection-oriented TCP services with enhancements to support the respective applications. The reasons for using
UDP range from simplicity of implementation to predictable effect on network operations. Protocols such as TFTP, when combined with UDP being simple to implement in constrained
code spaces as may be found in diskless systems. In the case of network management protocols such as SNMP, UDP can be used without running the risk of piling additional traffic
onto networks that may already be stuck in congested states.
Where To From Here...
The tremendous growth of the Internet has led to a new series of problems with the existing TCP/IP suite. Perhaps the most chronic problem will be the consumption of the address
space provided by the existing 32-bit services. This problem, topological flexibility, performance, and several others are being addressed in the Internet Protocol, Next Generation (IPng)
efforts. At this point, the IPng has consisted of several working groups that have published request for comments. One of the major difficulties in establishing and fielding the IPng is
that systems based on the new protocol will need to provide backwards compatibility with the existing IP based systems. For now, IP is the defacto standard for Internet access, with
the growth of activity on the Internet fueling continued research and sophistication in the supporting protocols.
If you require additional information on the Internet protocols and engineering, there are a wealth of on-line and written resources that are available. Douglas Comer's series on
"Internetworking with TCP/IP" provides a comprehensive look at the protocols. All of the RFCs can be obtained through a number of on-line resources. If you lack access to the
Internet, the
RFCs
can also be obtained in an electronic form through a useful CD publication, the Internet Info disk that is distributed by Walnut Creek, Inc.

