V5 Protocol
Basic Principles
V5 is a standardized protocol suite for the connection of Access Networks (AN) to the Local Exchange (LE).
The Access Network itself typically has PSTN and ISDN interfaces (user ports) to the customer.
The V5 interfaces are based on G.703/G.704 interfaces at 2048 kbit/s (E1).
V5.1 is a single 2048 kbit/s interface, whereas V5.2 may consist of one or up to sixteen 2048 kbit/s links,
provisionable by the operator.
Note that Access Network (AN) is often also referenced as Line Termination (LT) and Local Exchange (LE) as Exchange Termination (ET).
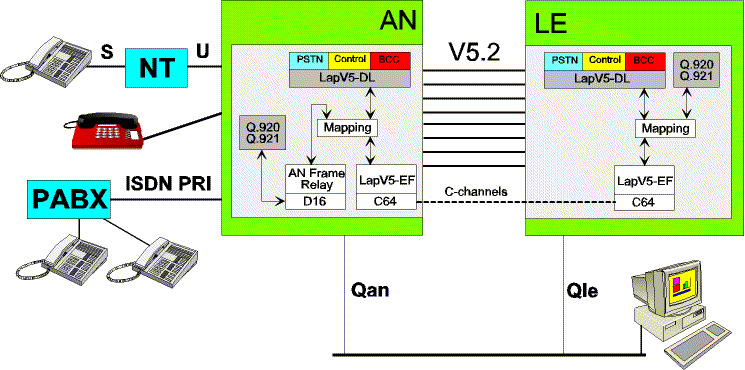
Figure 1 - V5 Principles
Time slot 0 (TS0) of the 32 time slots is always used for frame alignment, error reporting and error performance
monitoring using cyclic redundancy check procedures. In case of V5.2 links, TS0 is additionally used to verify the
correct physical connection of a 2048 kbit/s link. Up to three time slots on each 2048 kbit/s link may be assigned
as so-called communication channels (C-channels). C-channels carry PSTN signalling, ISDN D-channel information,
control information and, in case of V5.2 the bearer channel connection protocol (BCC) and the protection protocol.
All 64 kbit/s time slots not provisioned as C-channels are available as PSTN or ISDN bearer channels or may
carry analogue or digital leased lines.
Major differences between V5.1 and V5.2 interfaces
- V5.1 uses only one 2048 kbit/s link whereas V5.2 may use up to sixteen 2048 kbit/s links on one interface.
- V5.1 does not support concentration whereas V5.2 is inherently designed to support it using a dedicated protocol known as the Bearer Channel Connection (BCC) protocol.
- V5.1 does not support ISDN primary rate access user ports whereas V5.2 does.
- V5.1 has no concept of communication channel protection whereas this function is available for V5.2 when that particular V5.2 interface uses more than one 2048 kbit/s link. A specific protocol, known as the protection protocol, is provided for this function.
- The control protocol for V5.2 is slightly different to that used for V5.1.
- A link control protocol is specified for V5.2 as multiple links have to be managed.
The V5.1 interface between an Access Network (AN) and the Local Exchange (LE) support the following access types:
- Analogue telephone access
- ISDN basic access (BA)
- Other analogue or digital accesses for semi-permanent connections without associated out-band signalling information
The V5.2 interface between an Access Network (AN) and the Local Exchange (LE) support the following access types:
- Analogue telephone access
- ISDN basic access (BA)
- ISDN primary rate (PRA/PRI)
- Other analogue or digital accesses for semi-permanent connections without associated out-band signalling information
Frame Structure of 2M Signal
|
Sub- Multiframe (SMF) |
Frame Number |
Bits 1 to 8 of the Frame (TS 0) |
| |
|
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
|
I
|
0
1
2
3
4
5
6
7 |
C1
0
C2
0
C3
1
C4
0 |
0
1
0
1
0
1
0
1 |
0
A
0
A
0
A
0
A |
1
Sa4
1
Sa4
1
Sa4
1
Sa4 |
1
Sa5
1
Sa5
1
Sa5
1
Sa5 |
0
Sa6
0
Sa6
0
Sa6
0
Sa6 |
1
Sa7
1
Sa7
1
Sa7
1
Sa7 |
1
Sa8
1
Sa8
1
Sa8
1
Sa8 |
|
II
|
8
9
10
11
12
13
14
15 |
C1
1
C2
1
C3
E
C4
E |
0
1
0
1
0
1
0
1 |
0
A
0
A
0
A
0
A |
1
Sa4
1
Sa4
1
Sa4
1
Sa4 |
1
Sa5
1
Sa5
1
Sa5
1
Sa5 |
0
Sa6
0
Sa6
0
Sa6
0
Sa6 |
1
Sa7
1
Sa7
1
Sa7
1
Sa7 |
1
Sa8
1
Sa8
1
Sa8
1
Sa8 |
|
E CRC-4 Error Indication Bits
Sa4 to Sa8 Spare Bits, can be used for e.g. DCN purposes
C1 to C4 Cyclic Redundancy Check-4 (CRC-4) Bits
A Remote Alarm Indication |
Figure 2 - Multiframe Structure of G.703/G.704 2M Signal
| |
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
| |
|
|
|
Sa4 |
Sa5 |
Sa6 |
Sa7 |
Sa8 |
| |
Framing |
Sync. |
-- |
V5 |
-- |
Figure 3 - TS0 of G.703/G.704 2M Signal in V5.2 use
The Sa7 bit is used for link control purposes only if the interface is in V5.2 use, refer to ETS 300 347.
The usage of Sa4 bit for synchronisation purposes is optional and depends upon provisioning.
ISDN primary rate uses Sa4 to Sa6 for link management purposes.
V5 Protocols
The control and link control protocols provide the bidirectional information transfer required to:
- Control the operational status of individual user ports
- Control the operational status of 2048 kbit/s links (E1)
- Activation and deactivation of basic rate ISDN lines
- Link identification
- Coordinated and synchronized reprovisioning
In V5.2 the C-channels are protected against 2048 kbit/s link failures, if V5 consists of more
than a single 2048 kbit/s link. A protection protocol running on two 2048 kbit/s links in parallel controls the switch-over of C-channels in
case of a link failure. These two dedicated 2048 kbit/s links, carrying the protection protocol, are called
primary link and secondary link. The common bearer channel connection protocol (BCC) under control of the
LE side sets up connections on per call basis in the V5.2 case.
In the V5.2 case the control protocol and link control protocols, the BCC protocol and, if provisioned, the
protection protocol are always kept together in the TS16 of the primary 2048 kbit/s link of the V5.2 interface. All
other protocols may be assigned to TS15, TS16 or TS31 of any 2048 kbit/s link of the V5.2 interface by
provisioning. TS16 of the secondary 2048 kbit/s link also carries the protection protocol and is reserved as backup
c-channel for the TS16 of the primary link.
V5.1 uses just a single 2048 kbit/s link with a fixed association between timeslots and user ports.
In the V5.1 case the control protocol is always allocated to TS16. All other protocols may be assigned to either
TS15, TS16 or TS31.
Link control requirements and procedures
Since the V5.2 interface may consist of multiple 2048 kbit/s links, there is a need for link ID-verification and for blocking of a specific link. Two procedures have been defined for these functions and are performed through the link control protocol.
- Link-ID verification - The link-ID verification is a symmetrical procedure that shall be applied from both ends of the V5.2-interface links, when the interface Layer 1 Finite State Machine (L1-FSM) enters the normal state. If the procedure fails, the FSM shall return to the non-operational state. This procedure shall apply to all links, including the primary and secondary links. It may also be performed when permanently in the normal state, e.g. on a timed basis, or on a request from the Q-interface (AN/LE). This procedure shall apply even in the case of the single 2048 kbit/s V5.2 interface.
- Link blocking - For link-maintenance additional functionality is required for blocking a single 2048 kbit/s link of a V5.2 interface. Link blocking is an asymmetrical procedure, where the AN may request the blocking of a link, but the LE decides, as master of the service. The LE releases any switched connection on the requested link as appropriate to the service and, in due time, re-establishes semi-permanent and pre-connected connections onto other links within the same V5.2 interface. The LE shall use the protection protocol to move affected logical C-channels, if at all possible. This procedure may be applied even in the case of the single 2048 kbit/s V5.2 interface.
Bit rates lower than 64 kbit/s are not supported directly. They are seen as user applications within a 64 kbit/s B-channel in the PRA. One or more B-channels in the PRA may be used for the optional permanent line capability or semi-permanent leased line service. Multi-rate bearer services, which may use H0, H12 or other multislot channels between userport and LE are also supported by any V5.2 interface supporting ISDN-PRA using the appropriate ISDN signalling systems.
Control principles
The following general requirements have been defined for both the ISDN-BA port and the ISDN-PRA port. They shall be relevant for the PSTN ports as well if not stated otherwise:
- The responsibility for call control resides in the LE, i.e. the AN may have no knowledge of the call state during normal operation of the V5.2 interface.
- The access management in the AN and the service management in the LE each maintain their FSMs and protocol entities and communicate over the V5.2 interface.
- FSMs are required for each user port and for the 2048 kbit/s interfaces as well as protocol entities for the layer 2 links, in both the AN and the LE
- Port blocking request, for non-urgent port maintenance via the Q-interface of the AN, can only be granted by the LE, i.e. blocking request should not interfere with on-going calls, calls being set up or cleared down or semi-permanent connections.
- Urgent port maintenance requested via the Q-interface of the AN shall be indicated to the LE irrespective of the state in the LE i.e. "immediate blocking" effective immediately, but new state to be synchronized with the LE.
- Detected layer 1 failures related to bearer channels within the failed 2048 kbit/s links shall result in the calls being cleared. Detected layer 1 failures relating to physical C-channels within a failed 2048 kbit/s link shall result in the protection protocol reassigning these C-channels if it has sufficient resources to do so.
- It is required that detected anomalies and other events are reported to the associated management within theAN or LE and logged.
- When a port is blocked, originating calls are not possible and terminating calls should be treated by the LE as if the port is out of service according to the national protocol.
- The LE shall know the transmission quality level relating to user ports via "grading" messages from the AN to the LE which do not affect the port status FSMs. These messages contain grading information to be registered in the LE. The LE may use this information to decide whether a requested service should be delivered or not.
- Loop-backs shall only be applied when the port is in the blocked state. This function is under the control of the AN. The execution of failure localization within the AN and the user port is the responsibility of the AN. Active testing which interferes with the service under the responsibility of the LE, shall not be carried out until the port is blocked (FSM in blocked condition) by the LE.
- There shall be a mechanism to identify individual V5 interfaces, and the labels of their current and new provisioning variants. The provisioning variant is a unique label of a complete provisioning data set applied via the Q-interfaces.
- It shall be possible to identify each individual 2048 kbit/s link on a V5.2 interface. A symmetrical procedure for checking the identity of 2048 kbit/s links shall be applied on any restoration of frame alignment and after reprovisioning (which may or may not affect V5.2 links).
- It shall be possible to block an individual 2048 kbit/s link for a V5.2 interface. The AN may issue a request, but the LE decides: for switched connections it will wait for calls to terminate, semi-permanent and AN reserved connections will be re-established onto other links. LE system management will use the protection protocol to move affected logical C-channels before a 2048 kbit/s link is blocked. Using a slightly different mechanism, the AN may perform an immediate block of a designated 2048 kbit/s link.
- 2048 kbit/s links may be removed from service within a V5.2 interface for maintenance purposes via Qle and Qan with the support of the V5.2-interface link control protocol. They will be brought back into service, also using the V5.2-link control protocol.
- Individual bearer channels within a V5.2 interface may be barred from use via Qle.
Bearer Channel Connection (BCC)
The BCC protocol is used to allocate bearer channels on a specific 2048 kbit/s link to user ports, generally on a call by call basis. The bearer channels allocated by means of the BCC protocol but not on a call by call basis are given below:
- The semi-permanent leased line connection - These use one or more bearer channels which are assigned to user ports using Qle and are set up using the BCC protocol.
- The pre-connected bearer channels - These use one or more bearer channels which are assigned to user ports using Qle and are set up using the BCC protocol.
Protection
The protection protocol is used in the case of interfaces with more than one 2048 kbit/s link.
It is required that the link control, the control, and the BCC protocols have a communication path
over the V5.2 interface, even in the event of one 2048 kbit/s link failure (i.e. primary or secondary link).
The protection protocol has the responsibility to ensure that there is a method by which entities in the
LE and AN can communicate for the purpose of protecting logical C-channels in the case of a single link failure,
if standby physical C-channels are provisioned. In the event of protection switching being required for logical
C-channels, it is the responsibility of the protection management function to initiate the switch-over in a
controlled manner using the protection protocol.
Standards
Standards dealing with V5 issues are available both from ETSI and ITU-T.
A small subset is given below:
- G.964: V-Interfaces at the Digital Local Exchange (LE);
V5.1 Interface (based on 2048 kbit/s) for the support of Access Network (AN)
- G.965: V-Interfaces at the Digital Local Exchange (LE);
V5.2 Interface (based on 2048 kbit/s) for the support of Access Network (AN)
- Q.920: Digital Subscriber Signalling System No.1 (DSS1); User-Network Interface Data;
Link Layer; General Aspects
- Q.921: Digital Subscriber Signalling System No.1 (DSS1); User-Network Interface Data;
Link Layer Specification (LapD)
- ETS 300 324-1: V5.1 Interface for the support of Access Network (AN)
- ETS 300 347-1: V5.2 Interface for the support of Access Network (AN)
- ETS 300 376-1: Q3 Interface at the Access Network for configuration of V5 Interfaces and
associated user ports
- ETS 300 377-1: Q3 Interface at the Local Exchange for configuration of V5 Interfaces and
associated customer profiles
- ETS 300 378-1: Q3 Interface at the Access Network for fault and performance management of V5 Interfaces and
associated user ports
- ETS 300 379-1: Q3 Interface at the Local Exchange for fault and performance management of V5 Interfaces and
associated customer profiles

